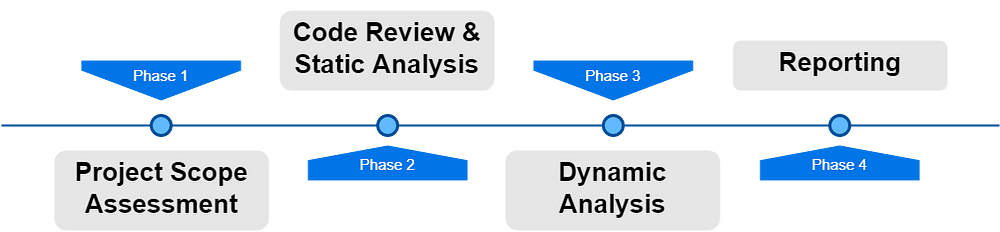
Phases of a Smart Contract Audit

Is there a trick or process to audit your Smart Contract effortlessly?
Yes, there is. Follow my lead!
Smart contracts are the building block of the blockchain. If there is any single vulnerability exists then the impact will be big. To avoid such incidents every company must do a smart contract audit. But web3 is new, and so are smart contracts. Most companies are therefore unaware on how to conduct out this procedure.
No worries we are here to help you!
In this blog, We’ll look at the prerequisites for doing a smart contract audit.
Target audience:
Organizations just entering the web3
Organizations that will be receiving audit projects
People who are curious to learn
Documentation:
The first and foremost thing is the documentation. When giving audit projects to other audit firms, The client must provide documentation to the auditors. Then only they can understand the architecture. It should be crisp and clear, and it should explain all the functionalities of the smart contract.
Questionnaire:
After looking into the documentation, the auditors will have some questions about the contracts for sure. It is the responsibility of the client to answer these questions or connect them with the developers who created the smart contracts.
Static code analysis:
This is where the actual auditing starts. Auditors will read through the source code and will try to find the vulnerabilities. But of course, during static code analysis, we may miss something. So the next step could be automated analysis.
Automated analysis:
In automated analysis, auditors will run a set of tools on the contracts. This technique is more efficient than static code analysis. But the problem with the automated analysis is it will have a lot of false positives. we can’t blindly trust the results from the tools. To increase the efficiency of the audit, auditors use another technique called Dynamic analysis.
Dynamic analysis:
In dynamic analysis, auditors will run the code and write test cases to find vulnerabilities. They will try to exploit every function with some known vulnerabilities such as reentrancy, front running, and overflows. Then they will look for functional bugs, logical bugs, and gas optimization bugs.
Report generation:
Now we are at the end of the audit phase. The bugs which are found will be consolidated into the report and will be sent to the client. Note that this will be the “First audit report” that will be sent to the client. Once the client fixes all those issues, the auditors will do one final round of testing and mark it as “Fixed” in the report.
