Public Key Cryptography – The Building Block of Web 3.0

Web 3.0 depends heavily on public key cryptography: From crypto wallet address to digitally signed transactions, everything uses public key cryptography. So let’s take a look at how it works.
Cryptography
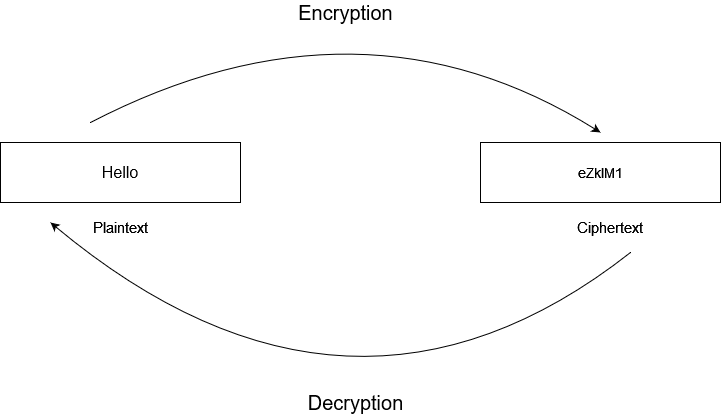
Cryptography is the field that relates to the security of communications data. The data to be secured is known as plaintext, which is then converted to an unintelligible form, known as the ciphertext. This process is called encryption, while the reverse is known as decryption.
Symmetric and Asymmetric Encryption
There are two different kinds of encryption – Symmetric and Asymmetric
The process of encryption uses multiple different algorithms which can be chosen based on your needs. These algorithms take as input, the plaintext, along with an alphanumeric key which is then used during encryption and decryption.
Symmetric encryption algorithms like DES, AES use the same key for both encryptions as well as decryption. This is also known as private key cryptography, as the key used must be kept private, so as to prevent unauthorized entities from gaining access to the communication being encrypted.
Asymmetric encryption algorithms like ECC, RSA, etc use a pair of keys during the process. Either of these keys can be used for encryption, but an encrypted message can only be decrypted using the key not used during the encryption process. This is also known as public key cryptography.
Public Key Cryptography
Let us consider two people, Alice and Bob who are trying to communicate with each other using public key cryptography. Each of them has a pair of keys – a private key and a public key. A user’s private key is secret while their public key is available to others as well.
The communication between Alice and Bob proceeds as follows:
- Alice writes her message, which she wants to send Bob. This will be the plaintext.
- She then encrypts this message using Bob’s public key.
- She then sends this ciphertext to Bob using a transmission medium.
- Bob receives this message and decrypts it using his private key.
- He now has the plaintext and can read the message.
This communication is secure since the message in ciphertext format cannot be read by someone even if they manage to intercept it. Due to the message being encrypted using Bob’s public key, the only way it can be decrypted is using Bob’s private key, which only Bob has access to.
Crypto Wallets
One of the major applications of public key cryptography in Web 3.0 is the creation of digital cryptocurrency wallets, which can be used to hold various types of cryptocurrencies.
There are a number of popular cryptocurrency wallet services like Metamask, Coinbase Wallet, etc.
A wallet address looks something like this -0x244xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxAE2ab60
For every user, a pair of keys is generated similar to how the RSA algorithm works. The public key serves as the identifier for that crypto wallet, while the private key is used for digitally signing all transactions made by the wallet owner. Therefore, it is extremely important to make sure that you DO NOT REVEAL YOUR PRIVATE KEY to anyone, for any reason at all. Doing so enables them to steal all the money from your account by signing transactions on your behalf.
Worried about attackers targeting your smart contracts? Contact us today to get your smart contracts audited for any security issues!
Anshul
Anshul is a cybersecurity analyst at DeTaSECURE. He has helped multiple organizations secure their digital assets as a security professional. He holds certifications like CEH and AZ-900. You can reach out to him by Clicking Here.
